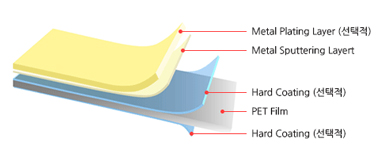
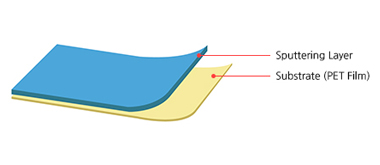
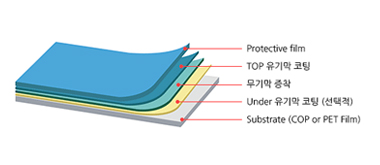
mind
mind
에스제이나노텍(주)은 혁신적이고 창의적인 기술과 제품으로 고객에게 보다
많은 가치와 만족을 제공하기 위한 무한 열정으로 미래를 준비해 가고 있습니다.
-
인간 중심
Anthropocentricism
-
창조 혁신
Innovation
-
미래 지향
Future-oriented
-
성장 추구
Growing